[ad_1]

Threat hunters have identified a new variant of Android malware. Mokhao It runs automatically on infected devices without requiring any user interaction.
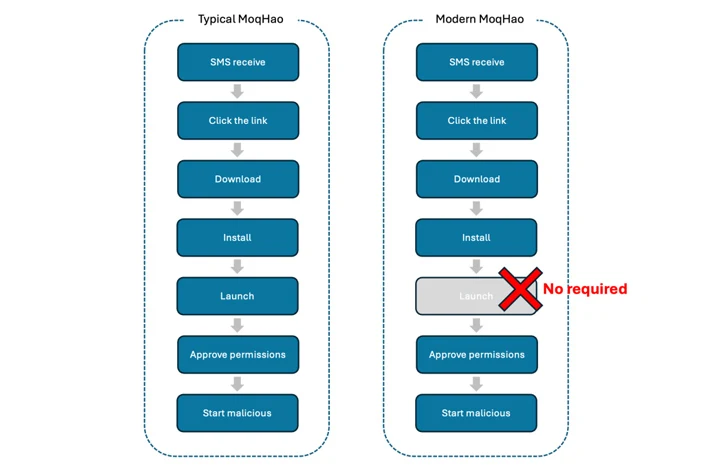
“While MoqHao typically requires users to install and launch an app to accomplish its desired goal, this new variant does not require that users do so,” McAfee Research said in a report released this week. Stated. “Malicious activity begins automatically while the app is installed.”
Targets for this campaign include Android users in France, Germany, India, Japan, and South Korea.
MoqHao, also known as Wroba and XLoader (not to be confused with the Windows and macOS malware of the same name), is an Android-based mobile threat associated with a Chinese financial cluster called Roaming Mantis (also known as Shaoye).

A typical attack chain begins with an SMS message containing a malicious link themed around package delivery, which when clicked from an Android device leads to malware deployment, but when accessed from an iPhone, victims are directed to Apple’s iCloud login page You will be redirected to a credential collection page disguised as .
In July 2022, Sekoia detailed a campaign that compromised at least 70,000 Android devices in France. As of early last year, an updated version of MoqHao was found to be able to infiltrate Wi-Fi routers and perform Domain Name System (DNS) hijacking, highlighting attackers’ efforts to innovate their arsenal. Ta.
The latest version of MoqHao continues to be distributed via smishing techniques, but what has changed is that the malicious payload is automatically executed upon installation, giving victims dangerous permissions without launching the app. It is an invitation to give. This behavior is caused by the HiddenAds malware.
Another improvement is that links shared in the SMS message itself are hidden using a URL shortener to increase the chances of a successful attack. The content of these messages is extracted from the bio (or description) field of fraudulent Pinterest profiles set up for this purpose.
MoqHao has several features that can secretly collect sensitive information such as device metadata, contacts, SMS messages, photos, call specific numbers in silent mode, and enable/disable Wi-Fi. It is equipped with the following functions.
McAfee said it reported its findings to Google, which is “already working on introducing mitigations to prevent this type of automatic execution in future Android versions.”
The development comes as Chinese cybersecurity firm QiAnXin has announced that a previously unknown cybercriminal organization named Bigpanzi is targeting Android-based smart TVs and set-tops in order to corral them into a botnet that performs decentralized denial. Box (STB) was revealed to be involved in a breach. Service (DDoS) attack.

The operation has been running since at least 2015 and is estimated to control a botnet consisting of 170,000 daily active bots, most of which are located in Brazil. However, since August 2023, 1.3 million different Brazilian IP addresses have been associated with his Bigpanzi.
This infection is possible by tricking users into installing booby-trapped apps that stream pirated movies and TV shows through creepy websites. The campaign was first revealed by Russian antivirus vendor Doctor Web in September 2023.
“Once installed, these devices turn into operational nodes within illegal streaming media platforms, supporting services such as traffic proxies, DDoS attacks, serving OTT content, and pirated traffic,” QiAnXin researchers said. I am.
“The possibility that Big Punji-controlled televisions and STBs could broadcast violent, terrorist, or pornographic content, or use increasingly persuasive AI-generated videos for political propaganda, poses a serious threat to social order and stability. poses a threat.”
[ad_2]
Source link


