[ad_1]

Russian-linked threat actor known as APT28 is believed to be linked to multiple ongoing phishing campaigns using decoy documents imitating governments and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and the Americas.
“The decoys uncovered include a mix of internal and public documents, as well as documents related to finance, critical infrastructure, executive engagement, cybersecurity, maritime security, healthcare, business, and defense industry production. It also includes documents that may have been created by the actors,” IBM X said. -Fors said in a report released last week.
The technology company tracks its activities under the nickname ITG05. This activity is also known as Blue Athena, BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, and TA422. UAC-028.

This disclosure comes more than three months after adversaries were discovered using decoys linked to the ongoing Israel-Hamas war to distribute a custom backdoor called HeadLace. It was done.
Since then, APT28 has also targeted Ukrainian government agencies and Polish organizations with phishing messages aimed at deploying custom implants and information theft techniques such as MASEPIE, OCEANMAP, and STEELHOOK.
Other campaigns have exploited a security flaw in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to loot NT LAN Manager (NTLM) v2 hashes, allowing attackers to The possibility of stealing NTLMv2 hashes is increasing. Used for relay attacks.
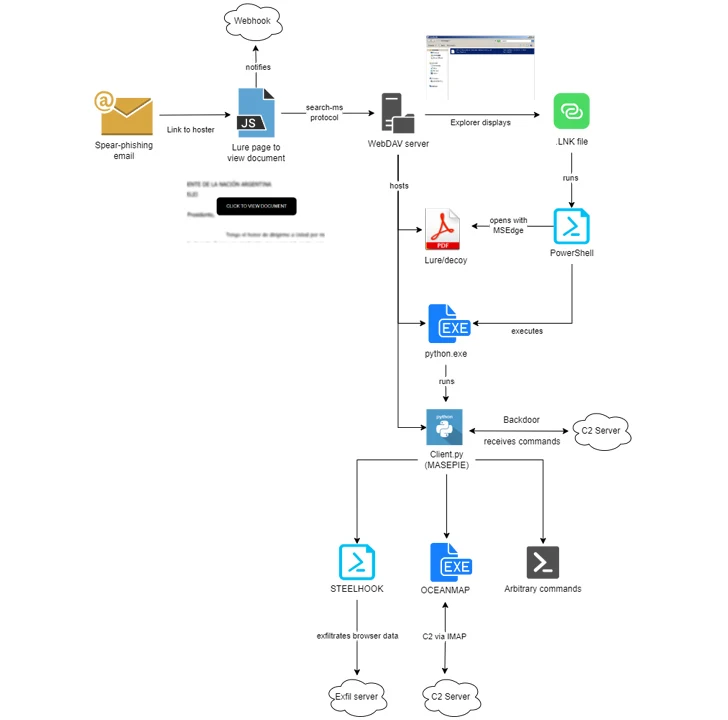
The latest campaign, observed by IBM X-Force from late November 2023 to February 2024, leverages the Microsoft Windows “search-ms:” URI protocol handler to trick victims into giving attackers control. downloads malware hosted on a WebDAV server.
There is evidence to suggest that both the WebDAV server and MASEPIE C2 server may be hosted on a compromised Ubiquiti router. The botnet that made up the Ubiquiti router was taken down by the US government last month.

The phishing attack impersonated organizations from countries including Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States, and used a combination of publicly available legitimate government and non-government documents to activate the infection. I will make it. chain.
“To update our methodology, ITG05 uses firstcloudit, a free hosting provider.[.]com stages the payload to enable continued operation,” said security researchers Joe Fasulo, Claire Zaboeva, and Golo Mühr.
APT28’s elaborate scheme culminates in the execution of MASEPIE, OCEANMAP, and STEELHOOK, which are designed to extract files, execute arbitrary commands, and steal browser data. OCEANMAP is characterized as a more sophisticated version of CredoMap, another backdoor previously identified as being used by the group.
“ITG05 continues to adapt to changing opportunities by consistently evolving its malware capabilities, offering new infection techniques, and leveraging off-the-shelf infrastructure,” the researchers concluded.
[ad_2]
Source link


