[ad_1]
On April 10, Apple sent a threat notice to iPhone users in 92 countries saying their devices were being “targeted by a mercenary spyware attack.” The alert, sent at 12pm PT, indicates that an attacker is attempting to “remotely compromise” your phone and is specifically targeting you because of “who you are or what you do.” I informed the recipient that there was a high possibility that Apple’s notice does not identify the alleged attacker or the recipient’s location.
Apple said on a dedicated support page that iPhone users who receive a warning of a mercenary spyware attack should seek assistance from a cybersecurity expert.
What did Apple’s latest threat notification say?
The emailed message was confirmed by TechCrunch and Reuters. It reportedly reads:
“Apple has detected that you are the target of a mercenary spyware attack that attempts to remotely compromise the iPhone associated with your Apple ID -xxx-.
“This attack may be specifically targeting you because of who you are or what you do. Although it is never possible to detect such attacks with certainty, , Apple has high confidence in this warning, please take it seriously.
“We are unable to provide further information about what caused this notification to be sent, as it may help mercenary spyware attackers adapt their behavior to avoid detection in the future.
“Mercenary spyware attacks like the one used by NSO Group’s Pegasus are extremely rare and much more sophisticated than typical cybercriminal activity or consumer malware.”
According to Apple, the notification also includes steps users can take to protect their devices, such as enabling Lockdown Mode, which restricts certain apps, websites, and features to reduce the attack surface for spyware. It contains.
What is a mercenary spyware attack?
Mercenary spyware attacks occur when spyware (malicious software used for surveillance purposes) is deployed to a target device by a third-party entity. The organization does this on behalf of its paying clients and aims to collect the necessary sensitive information or conduct surveillance without the sponsor’s direct involvement.
Spyware typically enters devices through software vulnerabilities or fraudulent activities such as phishing. Once installed, it can monitor your communications such as emails, text messages, and phone calls, track your location, steal your passwords, access your files, and remotely control your device. The collected data may be transmitted confidentially to the operator.
look: New GoFetch vulnerability in Apple’s M chip allows compromised computers to leak private keys
This spyware works without warning the user and can be deployed to any device that connects to the internet. Without detailed forensic analysis, it is very difficult to know whether a device is infected or not.
According to Apple’s support page, this type of targeted attack “has historically been associated with nation-state actors, including private companies developing mercenary spyware on behalf of governments,” such as NSO Group’s Pegasus.
Apple says mercenary spyware attacks are “significantly more complex” than regular malware attacks, use an unusual amount of resources against small groups, and can cost “millions of dollars to deploy.” It will take a while,” he added.
What are Apple Threat Notifications?
Apple has issued a threat notification (Diagram A) is “designed to inform and assist users who may be the individual targets of mercenary spyware attacks.” This notification does not necessarily indicate that the spyware has successfully landed on the user’s device. It does not mean embedded.
Diagram A
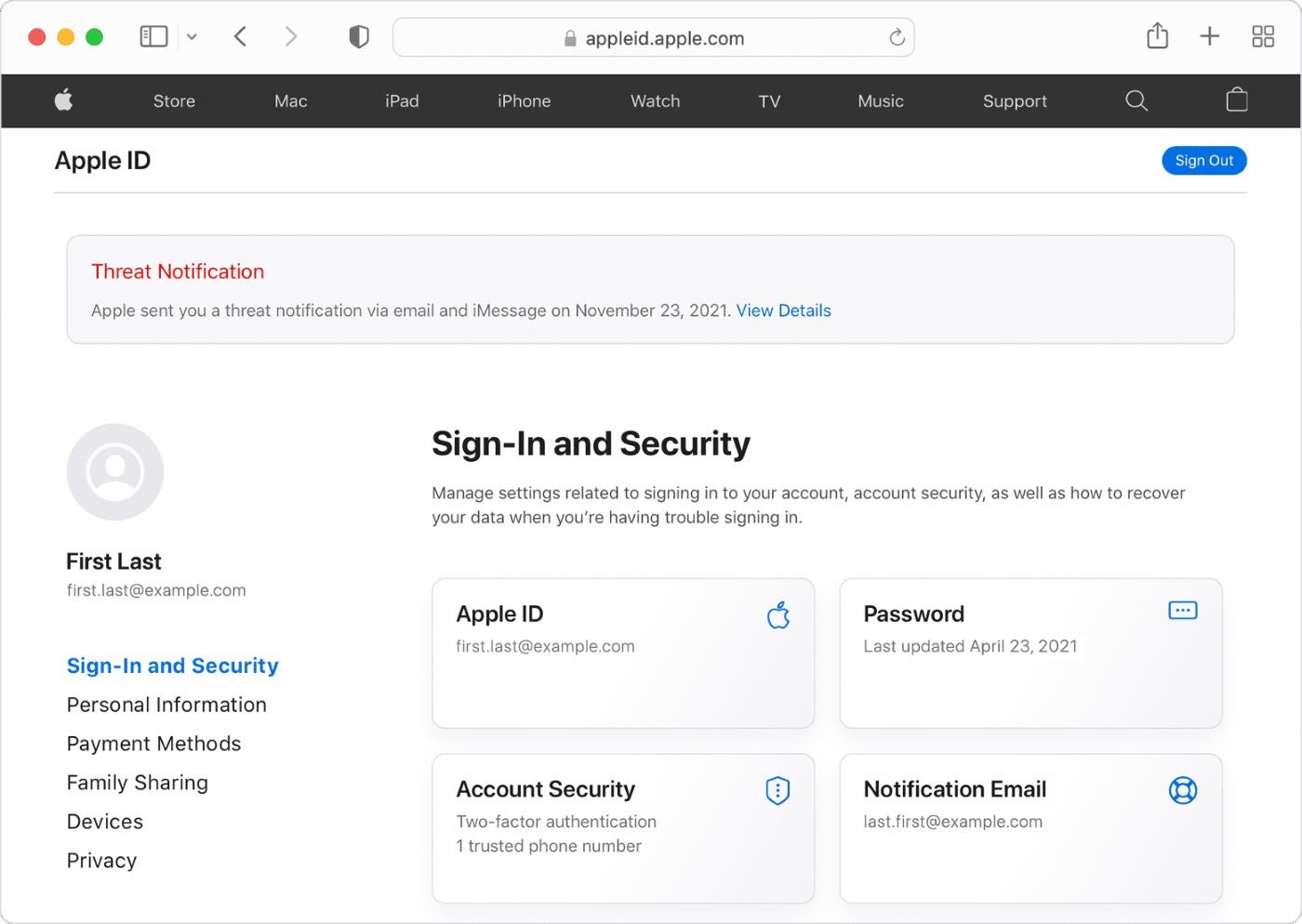
If we suspect you’ve been targeted, we’ll notify you on any device you sign in with your Apple ID. Messages will be sent by both email and iMessage, and a notification will appear at the top of the web page appleid.apple.com.
The tech giant said it uses “internal threat intelligence information and research” to detect mercenary spyware attacks, but could not reveal exactly what triggers a threat notification, adding that “in the future , as it could help mercenary spyware attackers adapt their behavior to evade detection.”
Apple says these threat notifications are “credible warnings” that a device has been targeted by a spyware attack, but that its research “can never achieve absolute certainty.” added.
According to Amnesty International, they and other civil society organizations conducted forensic tests on devices that received such notifications and reported that: Advanced spyware. ”
When did Apple start sending threat notifications?
Apple says it has been sending such threat alerts since 2021, and does so multiple times a year. To date, users in 150 countries have received notifications about similar attacks.
Apple last sent a threat notification on October 31, 2023, and the notification was received in multiple countries. Recipients were notified that they were being targeted by “state-sponsored attackers.” Apple has since stopped using the term state-sponsored in its threat notification policy, Reuters reported. In December 2023, Amnesty International revealed that Israeli surveillance firm NSO Group was behind the October attack after distributing Pegasus spyware to journalists.
Apple’s advice for users to protect their devices from malware
Research shows that 97% of all executives now access their work accounts through a personal device, and this number increases to 99% for executives. This creates a backdoor for cybercriminals to access sensitive corporate data through spyware, so employees must take steps to ensure their devices are secure.
look: Mobile device security policy (Tech Republic Premium)
Apple offers the following advice to all users to protect themselves from all types of malware.
- Update your device to the latest software as it includes the latest security fixes.
- Protect your device with a passcode.
- Use two-factor authentication and a strong password for your Apple ID.
- Install the app from the App Store.
- Use strong and unique passwords online.
- Don’t click on links or attachments from unknown senders.
[ad_2]
Source link


