[ad_1]
Mishal Rahman / Android Authority
TL;DR
- Cellular networks can determine a device’s location using network-initiated location requests.
- Your device’s privacy settings do not affect whether this request is accepted.
- However, new location privacy features in Android 15 may block these requests in non-emergency scenarios.
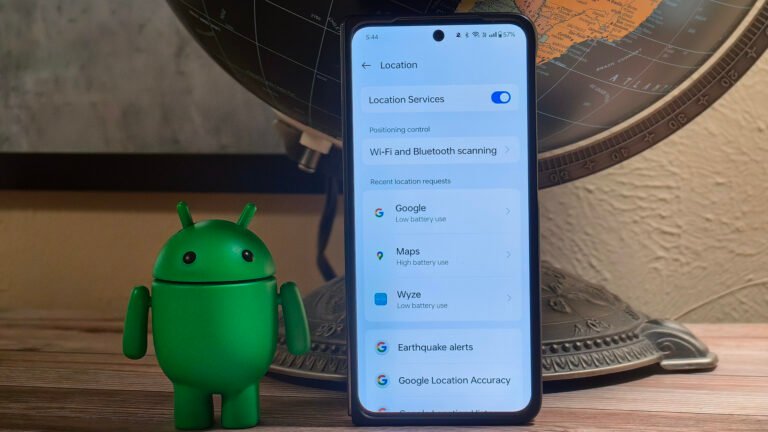
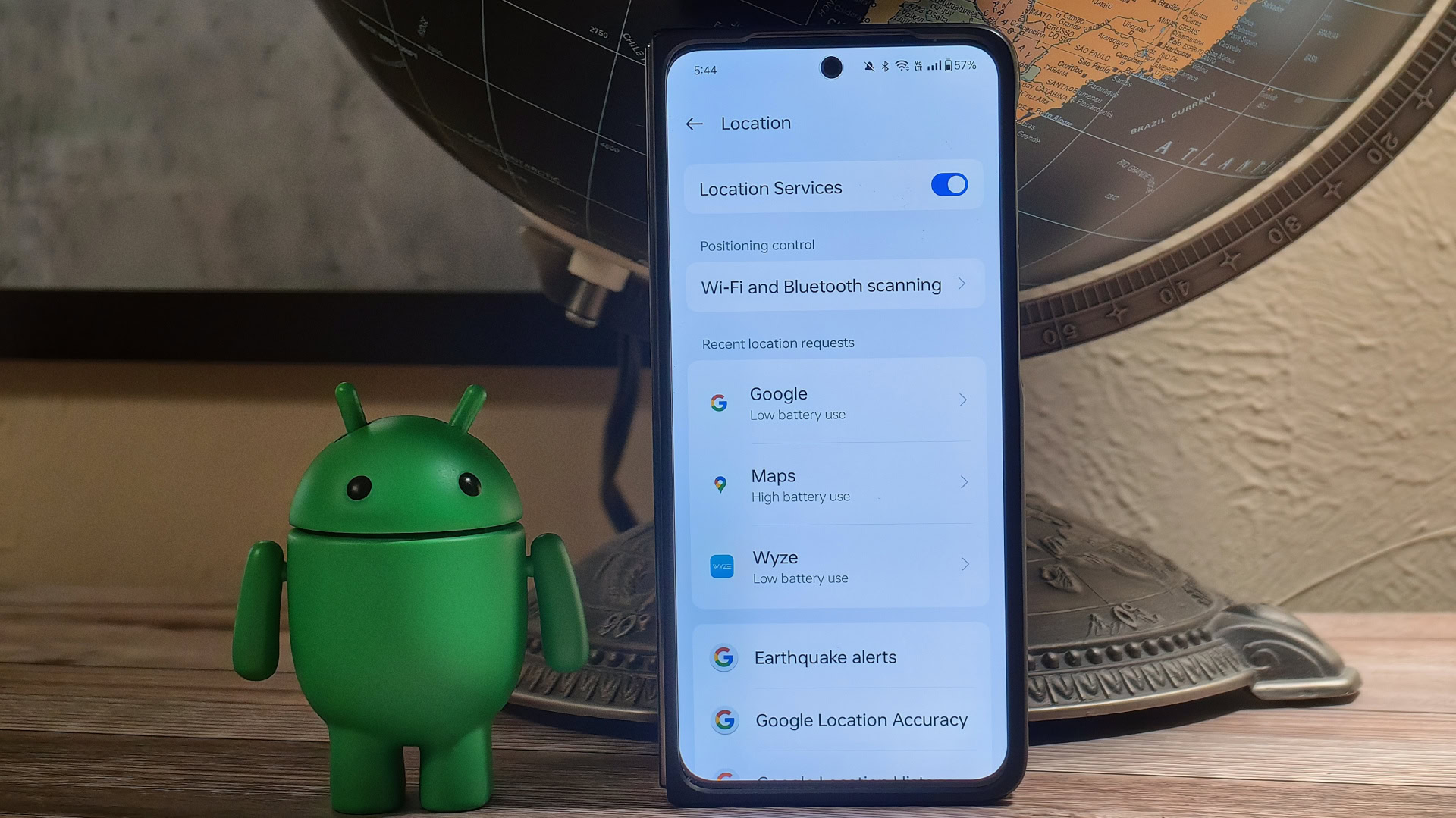
Your location is one of the most sensitive pieces of information an app can collect about you. It can show where you live, what people and businesses you visit, and in some cases, what you’re currently doing. That’s why Android provides robust privacy settings to control which apps can access your location. Still, the OS can do little to prevent carriers (mobile phone networks) from obtaining your location information. However, with Android 15, the OS may add a way to prevent your location data from being sent to your carrier.
The Android OS makes it easy to restrict or allow location access to Android apps. This is because these apps need to use APIs provided by the OS to obtain location information. However, the firmware running on the device’s cellular radio is a different story. Cellular radios in cell phones are often manufactured by manufacturers other than the cell phone’s OEM, and the Android OS often uses a well-defined hardware abstraction layer (HAL) for which the radio vendor has added support. It runs its own firmware that can only be interacted with using APIs. Starting with Android 15, radio vendors will be able to add support for Android’s new Location Privacy HAL. This allows you to instruct your radio not to share location data for non-emergency requests.
According to the GSM standard for location services, there are several ways to determine the location of your device. The most common scenario is Mobile Originated Location Request (MO-LR). This is when the device itself pings the network to get its current location. A Mobile Terminated Location Request (MT-LR), on the other hand, occurs when a third party, such as emergency services during a non-emergency call, requests the location of a device over the network. There is also a Network Initiated Location Request (NI-LR), where the cellular network itself triggers the process of locating the device. NI-LR is typically used for critical purposes when obtaining user permission is not possible or when immediate response is required, such as in an emergency.
Both MT-LR and NI-LR are typically used for emergency scenarios, but user privacy settings can influence whether a network satisfies MT-LR. However, the same is not currently true for his NI-LR. However, devices with radios that support Android 15’s new Location Privacy HAL can restrict location data from being shared to his NI-LR except in emergencies.
The wireless HAL’s Android source code implements new APIs for configuring location privacy settings. This API “updates current user settings for sharing location data” and “should be used by:” [the] For non-emergency use cases, use the radio before accepting network-initiated location requests. ” However, “the radio shall ignore this setting during emergency calls, emergency SMS, or emergency callback modes and continue to provide location information to network-initiated location requests.”
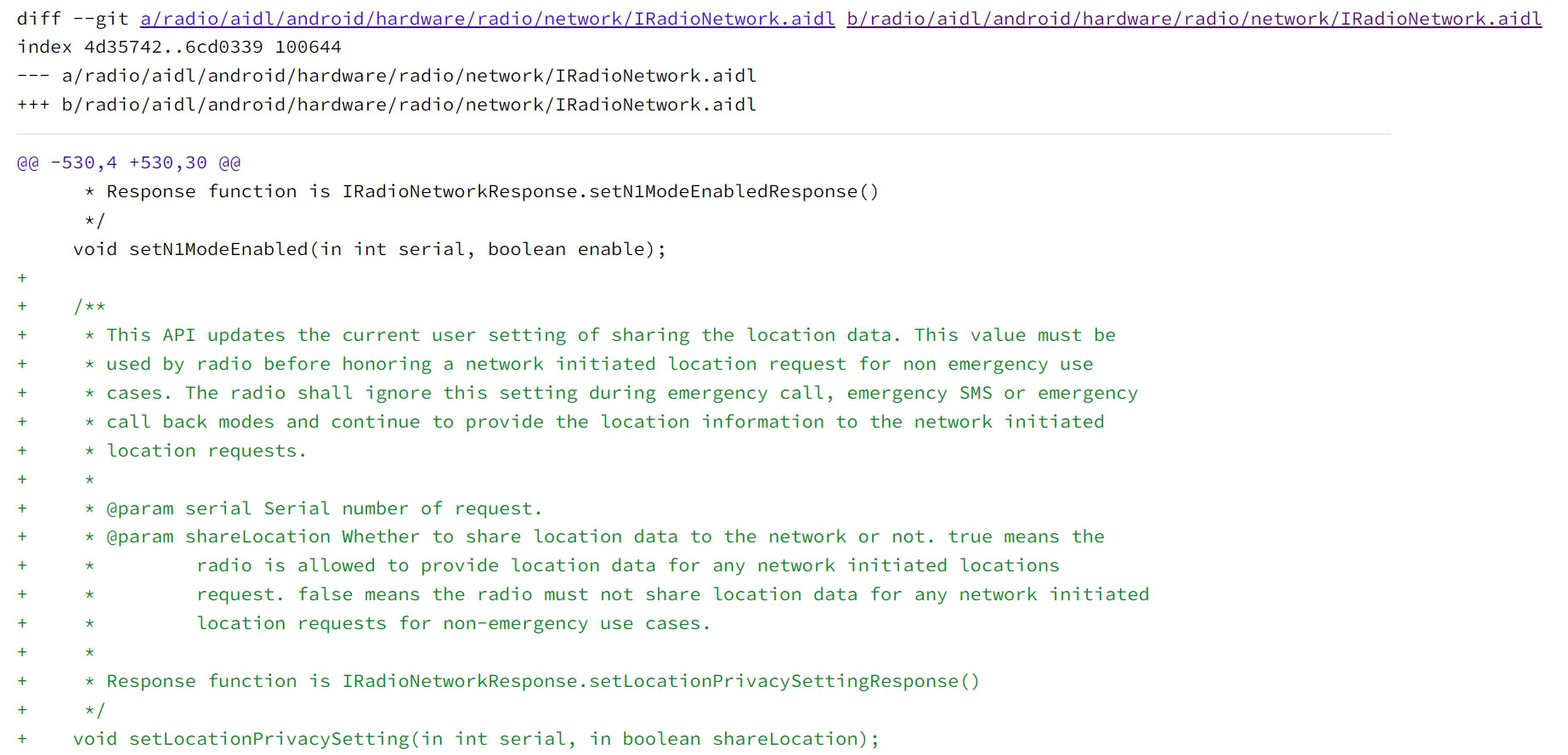
Mishal Rahman / Android Authority
This API was originally added in a patch to the wireless HAL source code in Android 14 QPR2, but was removed in a later patch. The reason the API was removed from Android 14 QPR2 was because this feature was migrated to “Android V” which refers to Android 15 (V is the first letter of Android 15’s internal dessert name, i.e. vanilla ice cream). . .
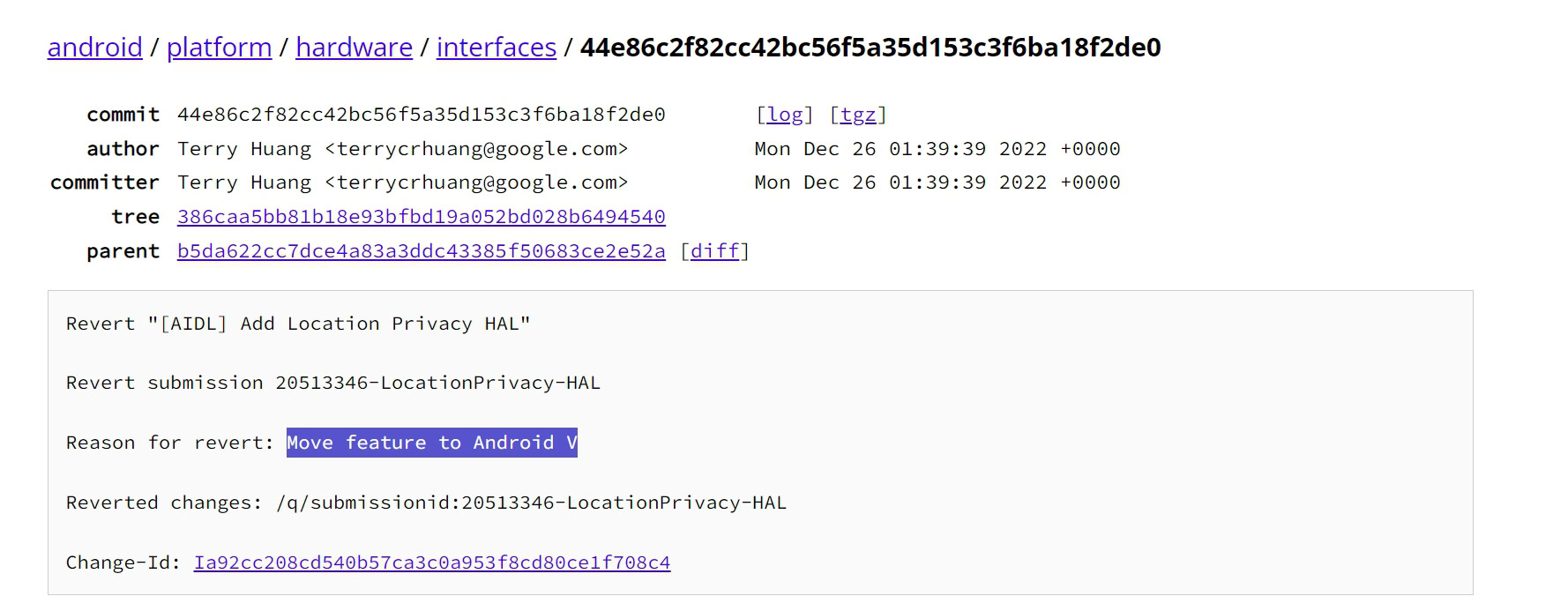
Mishal Rahman / Android Authority
This new location privacy feature requires wireless vendor support, so many devices upgrading to Android 15 may not support this feature. However, given that Google designs its own Tensor chipset, we can at least expect Google to add support in its own Pixel devices. It is known that the Tensor chipset uses Samsung’s Exynos modem, but it is possible that Google will have some say in what HAL features the modem supports.
This new location privacy feature will prevent your carrier from sending your NI-LR to access your exact location outside of an emergency situation, but it will likely prevent your carrier from providing your approximate location. I don’t think it will prevent you from getting it. Carriers continue to determine which cell phone towers your device connects to, and use the strength and angle of your device’s signal to the tower to find your device’s unique cellular ID to provide a general idea of your identity. location can be determined. Your location won’t be private when you’re connected to a cellular network, but at least with Android 15 you’ll have more control over when your location is shared. This feature also has the potential to mitigate attacks from “Stingray” devices, which mimic real cellular networks to trick devices into connecting and transmitting data.
[ad_2]
Source link