[ad_1]
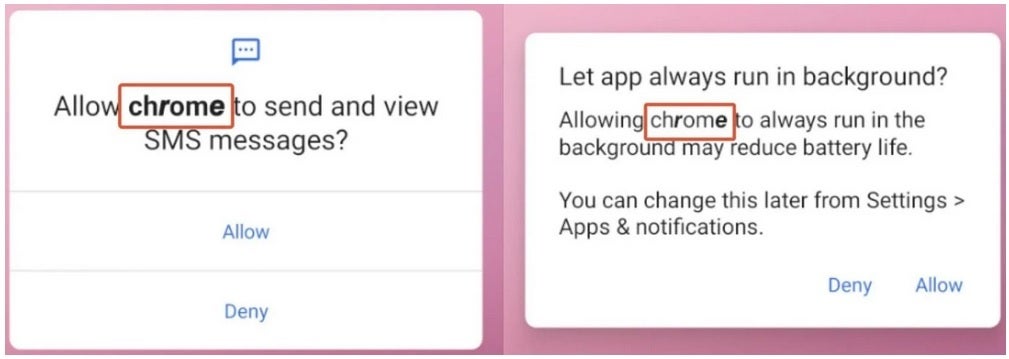

Fake permission requests appear to come from Google Chrome
“Malicious activity is automatically initiated while the app is installed,” McAfee said. “We are working to implement mitigation measures to prevent this.”
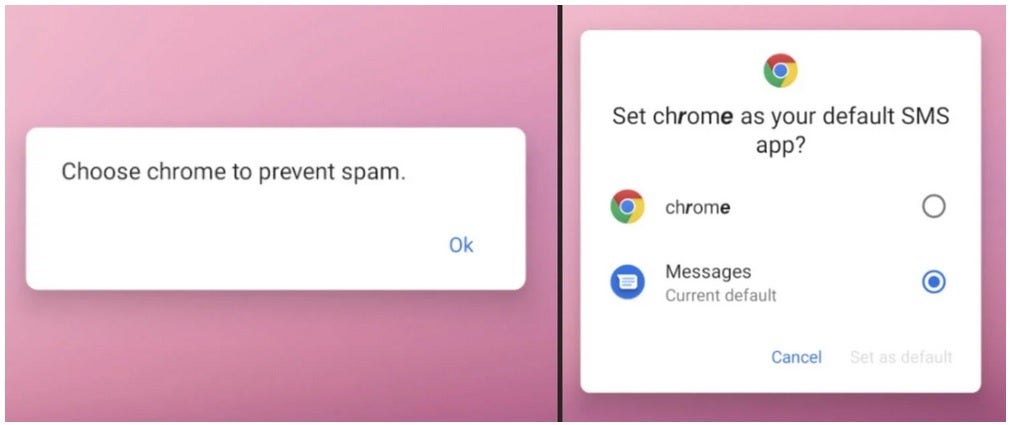

Another fake permit application
The malicious app sends permission requests disguised as coming from Google Chrome, asking for permission to send and view SMS (text) messages, and asking for permission to keep Chrome running in the background. And the biggest advantage is the permission to make “Chrome” the default SMS app. With all these permissions, the malware is used to send photos, text messages, contact list, and information about the hardware you are using (including your phone’s unique IMEI number) to a controlling server. . Yes, it’s very scary.
However, there are some things to consider here. Never click on shortened URLs in messages. Also, don’t sideload apps.
[ad_2]
Source link


