[ad_1]
Keeping your online accounts safe is a constant battle, which makes using passkeys and two-factor authentication (2FA) essential. Two-factor authentication codes add an extra layer of security and prevent hackers from breaking into your account, but some of the methods currently used to send these codes aren’t the most secure. However, this may actually change in Android 15, as a new line found in the source code suggests.
How does Google plan to protect login codes?
Google seems to be adding a new permission called “RECEIVE_SENSITIVE_NOTIFICATIONS”. This will likely be very limited and only available to certain system apps on your phone. This feature may work in conjunction with Android’s “NotificationListenerService” API, a system that allows apps to read and interact with notifications. This API is not automatically enabled and typically needs to be enabled manually in settings.
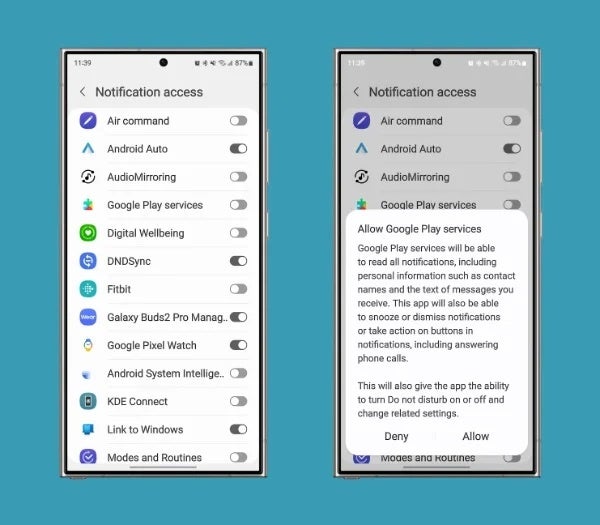

Current notification access setting is on android 14 | Source: Android Authority
The code snippet also shows that android 15 There is a feature called “OTP_REDACTION” that allows the 2FA code to be hidden directly on the lock screen. Android’s NoticeListenerService is extremely powerful and can be a valuable tool for malicious apps to access sensitive data.
[ad_2]
Source link


