[ad_1]
If you’re using Android, you’ll need to check the list of apps installed on your device. It studied more than a dozen Android apps with malicious code that could extract private messages from WhatsApp, record calls, copy contact numbers, and secretly take photos. This is because people are sounding the alarm.
This terrifying malware is known as VajraSpy and was discovered by a team from cybersecurity company ESET. The Patchwork APT group is believed to be behind the latest malware campaign. The group has been active since the end of 2015 and has deployed numerous malware during that time.
Half of the apps identified by the researchers were available on the Google Play Store, while the remaining six were only accessible through third-party app stores. Most of these were disguised as messaging or news apps, researchers claim.
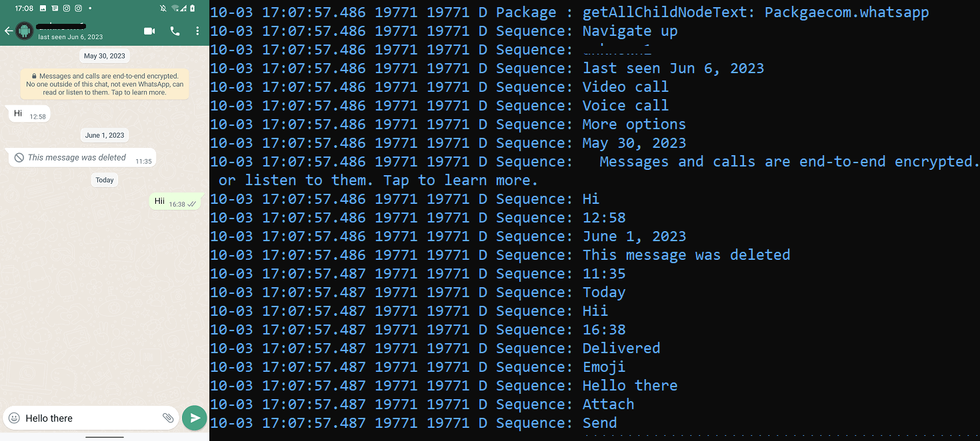
ESET researchers have shared evidence of VajraSpy malware that tracks messages sent within WhatsApp
ESET
Google removed the app from its digital store shelves as soon as it was reported by ESET’s team. However, this only prevents new users from installing malicious software…if you’ve downloaded these apps before, they’ll still be lurking on your handset.
Patchwork APT primarily targeted users in South Asia. According to Google Play Store statistics, some of these apps have been downloaded more than 1,000 times. However, the true number of people affected by this campaign will never be known, as third-party stores do not report download numbers.
ESET warns Android users that they should always avoid downloading unknown chat apps that are recommended by strangers or have few reviews in their store listings. This category has been a common and long-standing target for cybercriminals. looking for Infiltrate your device.
Messaging apps are extremely popular and require many permissions to work properly, including access to your camera, location data, files, and more. This level of access is very attractive to criminals looking to steal data.
This is not the first time that an app infected with VajraSpy spyware has entered the Google Play Store. Last year, Google had to: Eliminate a malware app with 2 million downloads.
Here are the latest apps reported by ESET researchers:
- Rafaqat رفاقت — Found on Google Play Store
- Privee Talk — Found on Google Play Store
- MeetMe — Found in Google Play Store
- Let’s Chat — Found on Google Play Store
- Quick Chat — Found in Google Play Store
- Chit Chat — Found on Google Play Store
- Hello Chat — Found in third-party app stores
- YohooTalk — Found in third-party app stores
- TikTalk — Found in third-party app stores
- Nidus — Found in third-party app stores
- GlowChat — Found in third-party app stores
- Wave Chat — Found in third-party app stores
In response to the latest report from the researchers, a Google spokesperson told security blog Bleeping Computer:
“Users are protected by Google Play Protect. Google Play Protect protects apps that are known to exhibit this malicious behavior on Android devices with Google Play Services. You can be alerted even if it comes from a source other than Play.
[ad_2]
Source link


